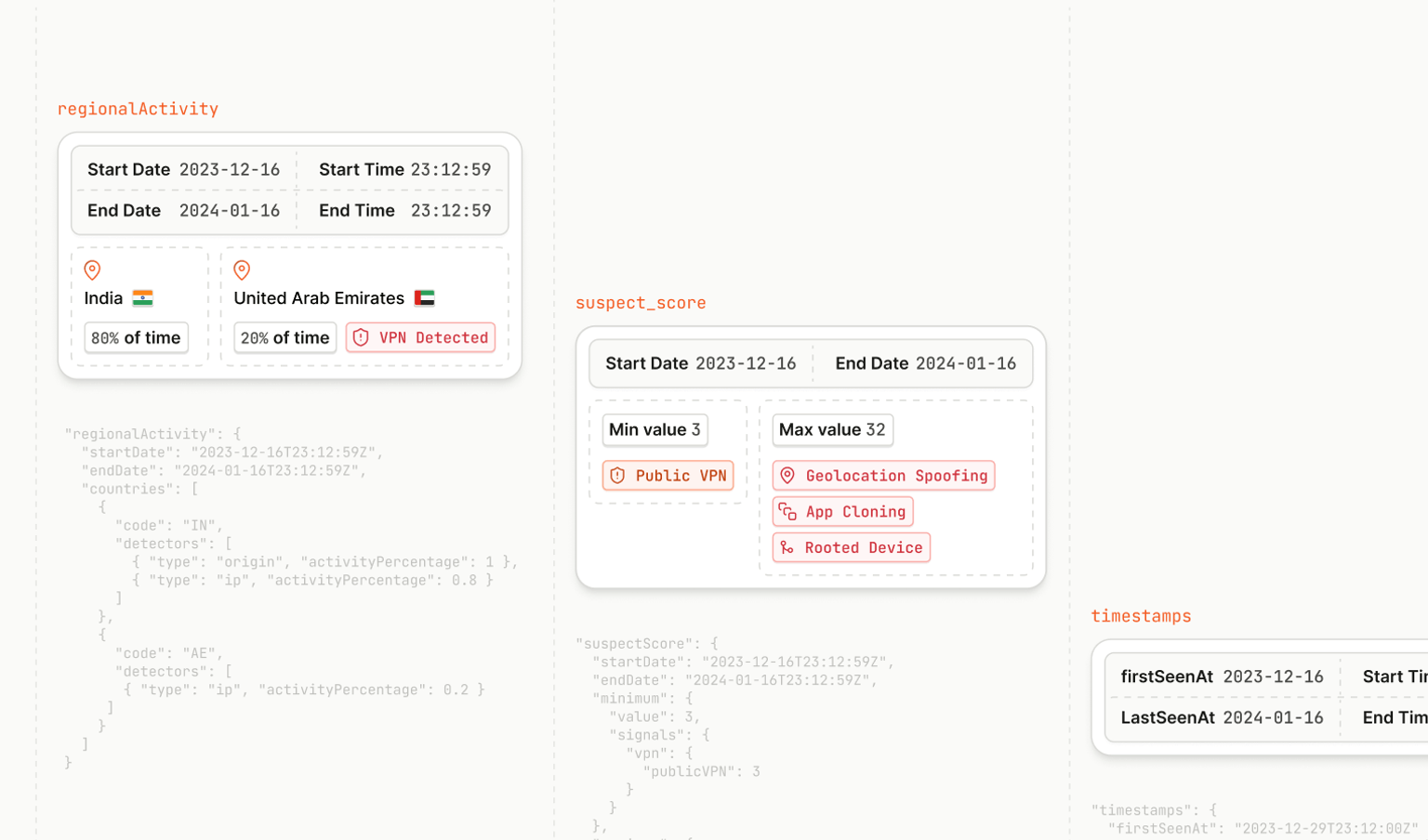
Pretending to be someone else is fun and games during a murder mystery party. However, when it comes to fraudulent attacks, it’s dangerous and costly when visitors stealthily veil themselves to commit acts of fraud on your site. Fraudsters are getting more intelligent and sophisticated in shielding their actual locations and identities to make it harder to prevent fraudulent activities.
Virtual machines are a widely accepted and recommended software testing and development method. However, fraudsters use that acceptance to their advantage to use virtual machines to anonymize their web visits and fool systems into thinking they are using a device they are not using.
In this article, we’ll discuss virtual machines, the types of virtual machines available, how they’re used for fraud, and why detecting virtual machines is essential as part of a robust fraud prevention strategy.
What is a Virtual Machine (VM)?
A virtual machine is a software application that mimics the functions of a physical computer. A virtual machine can run operating systems, even those not native to the computer system, and applications like a physical computer. Example: A virtual machine on an Apple computer could run Microsoft applications like a PC. VMs are often used in cloud computing environments to maximize resource utilization. They are also prevalent, and large cloud organizations like Google offer virtual machines (Google Compute).
What are the uses for a Virtual Machine?
Developers and engineering teams use virtual machines for a few common reasons during the development and maintenance processes.
- Software Testing & Development: Virtual machines allow pre-deployment testing on specific operating systems and applications, saving on time and device costs by not manually testing specific hardware and devices.
- Running Legacy Applications: Virtual machines can run older versions of software and operating systems, making it a more efficient and economical option for hosting legacy versions.
- Server Consolidation: Server consolidation is much easier with virtual machines by running multiple virtual servers on one physical server.
Types of Virtual Machines and Fraudster Techniques
There are primarily two types of virtual machines: System VMs and Process VMs.
- System Virtual Machines provide a substitute for a real machine. Google Compute is an example of this.
- Process Virtual Machines run a single program or process. An example is a Java Virtual Machine, which can run any Java application as if it were native to the operating system.
Fraudsters often use both types to employ ‘cloaking techniques’ to circumvent detection and disguise themselves to appear as real machines, making detection harder. They create numerous virtual environments, clone browser fingerprints, and even alter device configurations to mimic genuine user behavior. Additionally, Fraudsters might use a virtual machine to create a ‘safe’ environment where they can launch attacks without risking exposure or damage to their system.
Here are two successful uses of virtual environments for fraud attacks: gaining access to others’ virtual machine instances and using virtual machines to install malware. First, as reported in Wired, fraudsters gained access to VMware’s virtual machine system, Hypervisors. From there, they could go undetected and watch and run on computers utilizing virtual machines. Secondly, Symantec cybersecurity researchers discovered that fraudsters used VirtualBox, an open-source virtual machine, to aid in the attempt to install ransomware.
Understanding Virtual Machine Detection
Because of the increased risk of takeover, ransomware, and more attacks, detecting if a visitor or user is using a virtual machine is essential in a sophisticated fraud strategy. Virtual machine detection identifies whether a user's computer is a real machine or a virtual environment. This differentiation is crucial in detecting and preventing fraudulent activities, as fraudsters often use virtual machines to mask their identity and intentions.
With virtual machine detection as part of their fraud detection modeling, businesses can identify virtual machines and block or monitor interactions accordingly. The ability to detect a virtual environment helps companies differentiate between legitimate users and potential fraudsters, enhancing their security measures and reducing fraud risk.
The Role of Device Identification
Device identification plays a vital role in detecting fraud within the virtual environment. It involves gathering device attributes like IP address, operating system, browser type, etc., to create a unique device fingerprint. When combined with virtual machine detection, device identification provides a powerful tool to distinguish genuine users from fraudsters.
Consider using a device intelligence solution that already incorporates virtual machine detection as part of their device identifier, such as Fingerprint, the world's most accurate device identifier. With Fingerprint's Smart Signals, which includes Virtual Machine Detection, you identify traffic intent on committing fraud and make smarter real-time decisions by leveraging our Smart Signals into your existing fraud models.
Best Practices for Implementing Virtual Machine Detection
- Integrate with Existing Security Measures: Virtual machine detection should not replace but enhance your existing security measures. Integration with other fraud prevention technologies like behavioral analytics, device fingerprinting, and risk scoring can provide a comprehensive defense mechanism.
- Regular Updates: Given the rapid advancements in fraudulent techniques, updating the VM detection technology to recognize the latest cloaking techniques effectively is critical.
- User Experience: While security is paramount, it shouldn't compromise the user experience. Ensure your VM detection solution doesn't excessively delay website load times or disrupt user navigation.
- Data Analysis: Collect and analyze data on detected VMs to understand fraud patterns better and refine your fraud prevention strategies.
Virtual machines are a part of effective and innovative software development and shouldn't create a cause of concern when it's part of your visitor identification process and fraud prevention strategy.
New to device identification? You can try out Fingerprint Pro for free for 14 days.
Is it a fit? Speak with one of our product experts, who can walk you through it.